Keeping up with the flood of new software vulnerabilities (CVEs) is a constant challenge for any organization. What if you could receive tailored threat notifications within minutes of a critical vulnerability’s disclosure, focused only on the systems you use? That’s precisely what Framework Security’s agentic AI CVE advisory workflow delivers. In this post, we explore how customized CVE alerts and client-specific vulnerability intelligence are redefining proactive cybersecurity, particularly for organizations that leverage our vCISO cybersecurity support services.
The Problem with Traditional Vulnerability Monitoring
Many teams still rely on passive news monitoring or social media to learn about new vulnerabilities. Unfortunately, this reactive approach can leave you hours or even days behind. By the time a major tech blog or Twitter post alerts you to a critical CVE, attackers may have already started probing for targets. (In fact, threat actors begin scanning for vulnerable systems within 15 minutes of a CVE being made public.
Every minute counts, and traditional channels simply aren’t fast or focused enough. Moreover, the sheer volume of CVE announcements is overwhelming. Dozens of new CVEs are published daily, but not all apply to your environment. Sifting through irrelevant alerts wastes precious time and can lead to “alert fatigue,” in which genuinely dangerous vulnerabilities are overlooked. Without a more intelligent filtering mechanism, organizations either drown in noise or risk missing critical threats.
Introducing Framework Security’s Agentic AI CVE Advisory Workflow
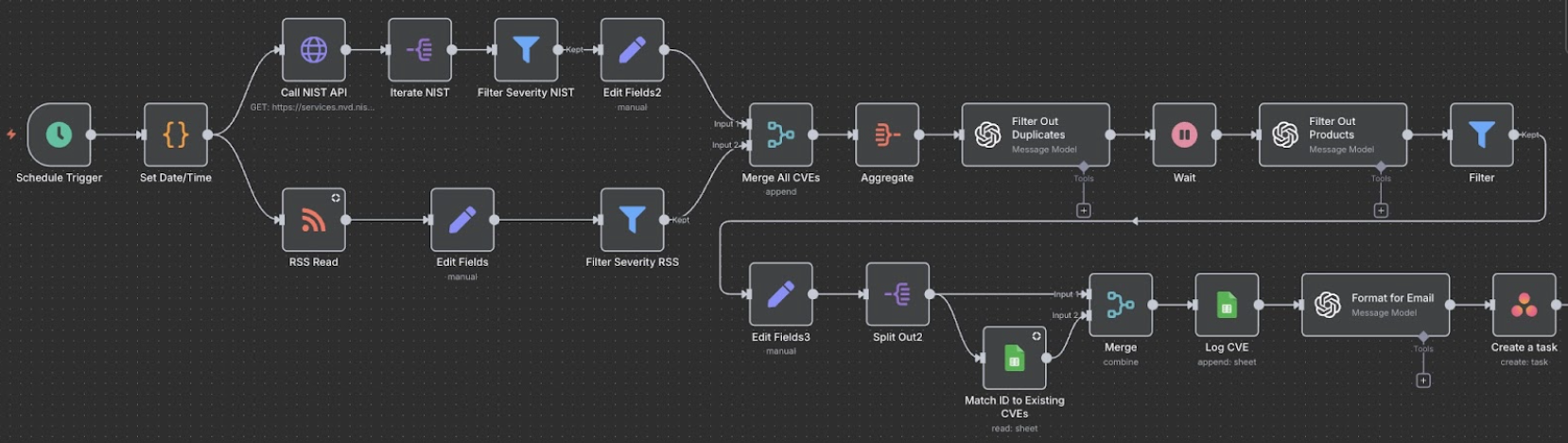
Framework Security has developed an agentic AI CVE advisory workflow that tackles these challenges head-on. This autonomous system acts as a 24/7 cybersecurity analyst, continuously monitoring vulnerability feeds and delivering tailored threat notifications to our clients. Here’s how it works:
- Real-Time CVE Monitoring: The system continuously retrieves data from trusted sources, including the NIST NVD database and industry-specific RSS feeds. New CVEs are detected within minutes of publication, ensuring that no critical updates go unnoticed.
- Smart Severity Filtering: To prioritize truly urgent issues, the workflow automatically flags vulnerabilities with a severity threshold (e.g., CVSS score > 8). This focus on high-impact threats means low-risk CVEs won’t distract you from pressing dangers.
- AI-Powered Analysis: What makes the workflow agentic (autonomous and action-taking) is its AI engine. The AI parses each CVE description and cross-references it against a knowledge base of our clients’ technology stacks and environments. It effectively asks: “Does this vulnerability affect any software, hardware, or service that Client X uses?” If not, the CVE is considered irrelevant for that client. If yes, it proceeds to the next step.
- Client-Specific Matching: Through intelligent filtering, clients receive alerts only about vulnerabilities that affect their technology stack and environment. For example, suppose you run a Windows Server and a specific database platform. In that case, you’ll be alerted about Windows or database-related CVEs that matter to you – but you won’t be spammed about Linux or network router flaws that don’t affect your assets. This client-specific vulnerability intelligence ensures that every alert in your inbox is actionable and relevant.
- Customized Advisory Creation: When a relevant CVE is identified, the system doesn’t just forward you the raw CVE bulletin. Our AI generates a concise, plain-language advisory tailored to the client. This includes the CVE ID and title, an overview of the issue, its potential impact on your systems, and recommended mitigation steps. The advisory distills the “most important thing to know” in one or two sentences, followed by key details and actionable next steps (e.g., patch availability, workarounds, or interim security measures).
- Immediate Alert Delivery: Finally, the workflow delivers these tailored threat notifications via email (and/or other preferred channels, such as Slack or a ticketing system integration) to the client’s security team or designated point of contact. This often occurs within minutes of the CVE’s public release—a speed practically impossible to achieve with manual tracking. In parallel, Framework Security’s internal team is notified via our operations tools (e.g., creating an Asana task for our analysts) to ensure we’re ready to assist the client as needed.
By combining automation with intelligent context awareness, our agentic AI workflow serves as an extra pair of eyes that never rests. It filters out the noise and zooms in immediately on the threats that you need to care about.
Customized CVE Alerts for Your Unique Environment
Personalization is central to how this service works. No two organizations have identical IT environments, so generic threat feeds rarely provide meaningful value. Our system delivers customized CVE alerts that reflect each client’s specific mix of platforms, applications, and cloud services.
During onboarding, Framework Security’s vCISO consultants and engineers collaborate with your team to understand your technology stack and the systems most critical to your business. Using that information, the AI builds a detailed profile of your environment, allowing it to filter new vulnerabilities with precision. The result is vulnerability intelligence tailored directly to your organization.
For example, if you’re a healthcare organization running VMware and connected medical IoT devices, your alerts will focus on vulnerabilities relevant to those systems, as well as any high-severity issues that could impact multiple industries. You won’t receive unnecessary advisories about technologies you don’t use.
This filtering ensures that the alerts you do receive truly matter. Each notification includes clear context: why the vulnerability is relevant to your environment and how to address it. This reduces noise, saves time, and allows your team to act quickly and confidently.
Personalization also prevents alert fatigue by ensuring that you’re only notified about issues that genuinely affect your systems. In a constant stream of cybersecurity news, having an intelligent filter helps your team prioritize effectively and focus resources where they’re needed most.
Faster Than Humanly Possible – A Critical Advantage
Speed is a key advantage of our agentic AI workflow. When a new critical CVE is published, every minute of delay in responding increases your risk. Our clients receive notifications about critical vulnerabilities within minutes of their release- much faster than the hours or days it can take to find out through passive channels or third-party reports. This proactive alerting can have a significant impact on your security posture.
To put it in perspective: without a system like this, a company might only hear about a new zero-day vulnerability later that day from a news article or the next day from a colleague sharing a tweet. By that time, attackers may already be exploiting the vulnerability. With Framework Security’s tailored notifications, you’ll likely see an advisory in your inbox shortly after the CVE is announced, including clear guidance on how to respond.
This means you can start assessing and mitigating the risk immediately, often before exploit code becomes publicly available. This rapid alerting narrows your window of exposure and gives your team time to apply patches, isolate affected systems, or take other defensive steps well before most others are even aware of the threat.
In essence, you’re consistently staying a step ahead, turning what used to be a reactive scramble into a calm, proactive process. In a world where attackers operate at machine speed, having AI working alongside your team isn’t just helpful, it’s essential.
Empowering vCISO Clients with Actionable Intelligence
Organizations using Framework Security’s virtual CISO (vCISO) services benefit from personalized, real-time alerting tailored to their specific needs. Acting as an extension of your leadership team, the vCISO provides both strategic guidance and hands-on oversight of your cybersecurity operations.
Effective decision-making at the CISO level depends on timely and relevant intelligence. Our vCISO service enhances this with customized Common Vulnerabilities and Exposures (CVE) alerts, delivered through an AI-supported advisory system that continuously monitors vulnerabilities specific to your business environment. It’s like having a dedicated vulnerability analyst who works around the clock to capture threats that matter most to you.
When a critical vulnerability emerges, your vCISO receives a focused briefing detailing the issue and its impact on your organization. This allows the team to quickly assess risk and recommend appropriate remediation steps, keeping your executive stakeholders informed and assured that the security risks are managed proactively.
This approach is particularly valuable for organizations without a large internal security team. By automating the initial research and triage of raw vulnerability data, the vCISO can concentrate on evaluating risk and guiding response efforts. This ensures that even smaller teams stay current with critical cybersecurity information and often get it ahead of competitors or peers.
Ultimately, this support helps reduce the chances of being caught by surprise with impactful vulnerabilities and demonstrates to auditors, customers, and boards that you have a mature, responsive risk management program. Framework Security’s vCISO service combines expert oversight with advanced automation to keep your organization secure and informed.
The Bottom Line: Personalized Alerts and Rapid Response Save the Day
Framework Security’s agentic AI CVE advisory workflow delivers two major advantages for cybersecurity operations: personalization and speed. By providing vulnerability alerts tailored to each client’s environment, it filters out unnecessary noise and ensures attention stays on the issues that truly matter to your organization.
Operating at machine speed means critical threats are identified and communicated faster, giving organizations a valuable head start in patching or mitigating vulnerabilities. This early awareness reduces the time window during which attackers can exploit known weaknesses.
Our approach makes proactive defense achievable by ensuring that high-priority information reaches the right people quickly. The AI-driven workflow shifts the balance in the defender’s favor—turning what is often a reactive process into a more strategic, informed response.
For organizations working with a vCISO or supplementing in-house security teams, the benefit is clear: vulnerability intelligence arrives in context, ready to act on. This targeted insight allows teams to focus on risk assessment and mitigation rather than sifting through raw data.
By combining automation with expert analysis, Framework Security helps its clients transform vulnerability management into a continuous, adaptive process- one that keeps leadership informed, teams efficient, and defenses aligned with emerging threats.
.png)